Seemorerocks
Tuesday 9 April 2024
Psychopathy in medicine
Saturday 24 February 2024
“SELF-SPREADING” VACCINES TAKE A DANGEROUS STEP FORWARD
This is the most important and frankly, frightening item of i
nformation that I have seen and so far the only source seems to be
the HIghwire.
I have on seen the following article from iCan, the Highwire’s legal arm.
ICAN UNCOVERS A POTENTIAL NEXT-LEVEL THREAT: “INHALABLE” SELF-SPREADING VACCINES THAT SPREAD LIKE A VIRUS
A new class of “encrypted RNA” vaccines are being developed where the
RNA would piggyback onto an existing wild virus and spread from person to person without any person’s knowledge or consent. Although this may
sound like science fiction, it is far from it. Two companies involved in this research have received millions of dollars from the federal government. A study using this technology on hamsters and the SARS-Cov-2 virus has already been completed and a Phase I trial on humans is in the works.
ICAN’s attorneys have already sent legal demands to all government
agencies involved.
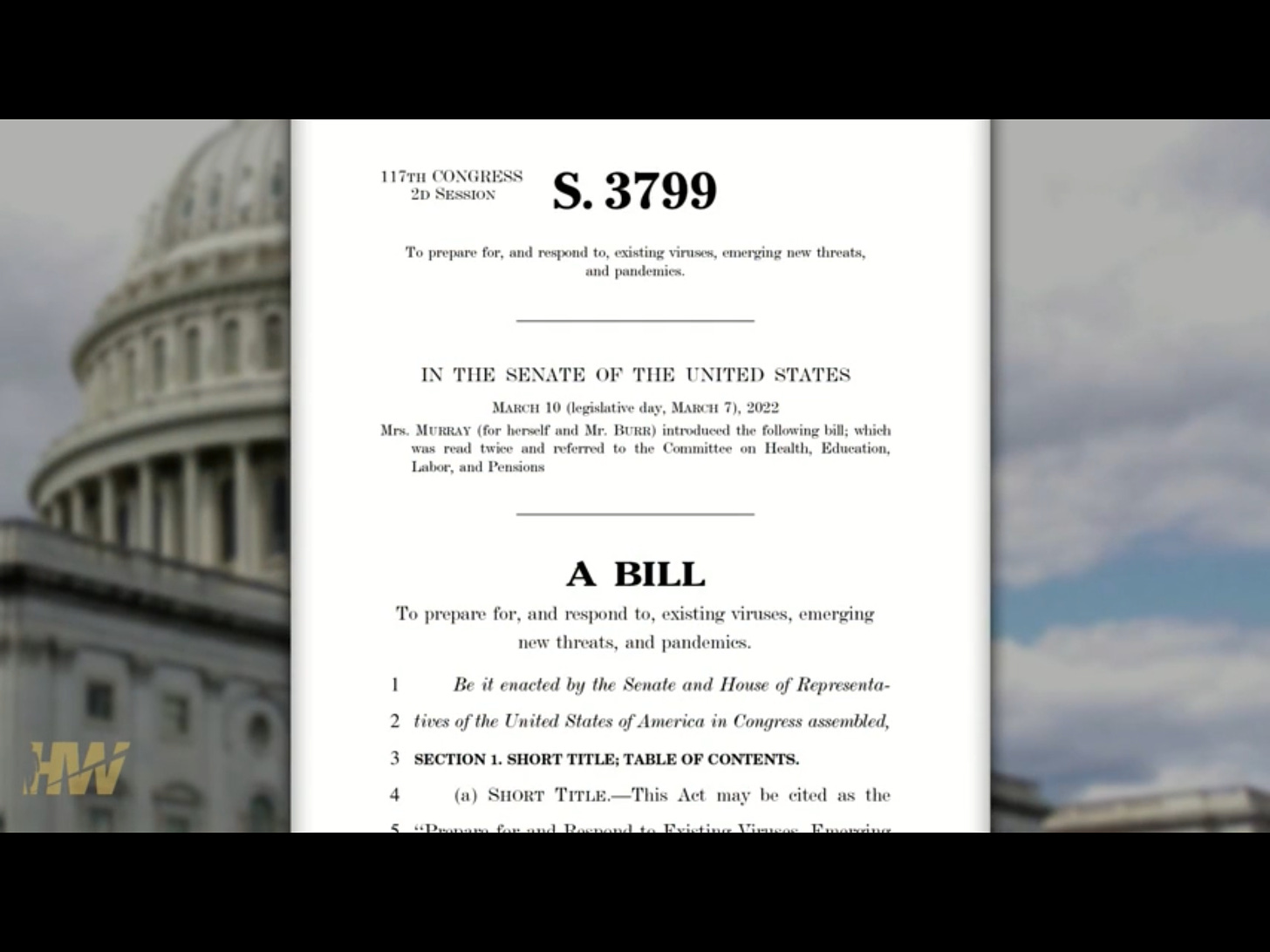
It seems the government and the military are so enthused about this new vaccine deployment technology that Congress tucked a law, the PREVENT Pandemics Act, into the 2023 omnibus appropriations bill to facilitate it. Among other things, the Act has a section dedicated to Platform Technologies that supports the “development
and review of new treatments and countermeasures that use cutting-edge,
adaptable platform technologies that can be incorporated or used in more than one drug or biological product.”
This item on the Highwire discusses this in detail
“SELF-SPREADING” VACCINES TAKE A DANGEROUS STEP FORWARD
Watch HERE
This is how Del Bigtree frames it (from the above video)
He goes on
Here are some of the articles referred to.
https://pubmed.ncbi.nlm.nih.gov/25017994/
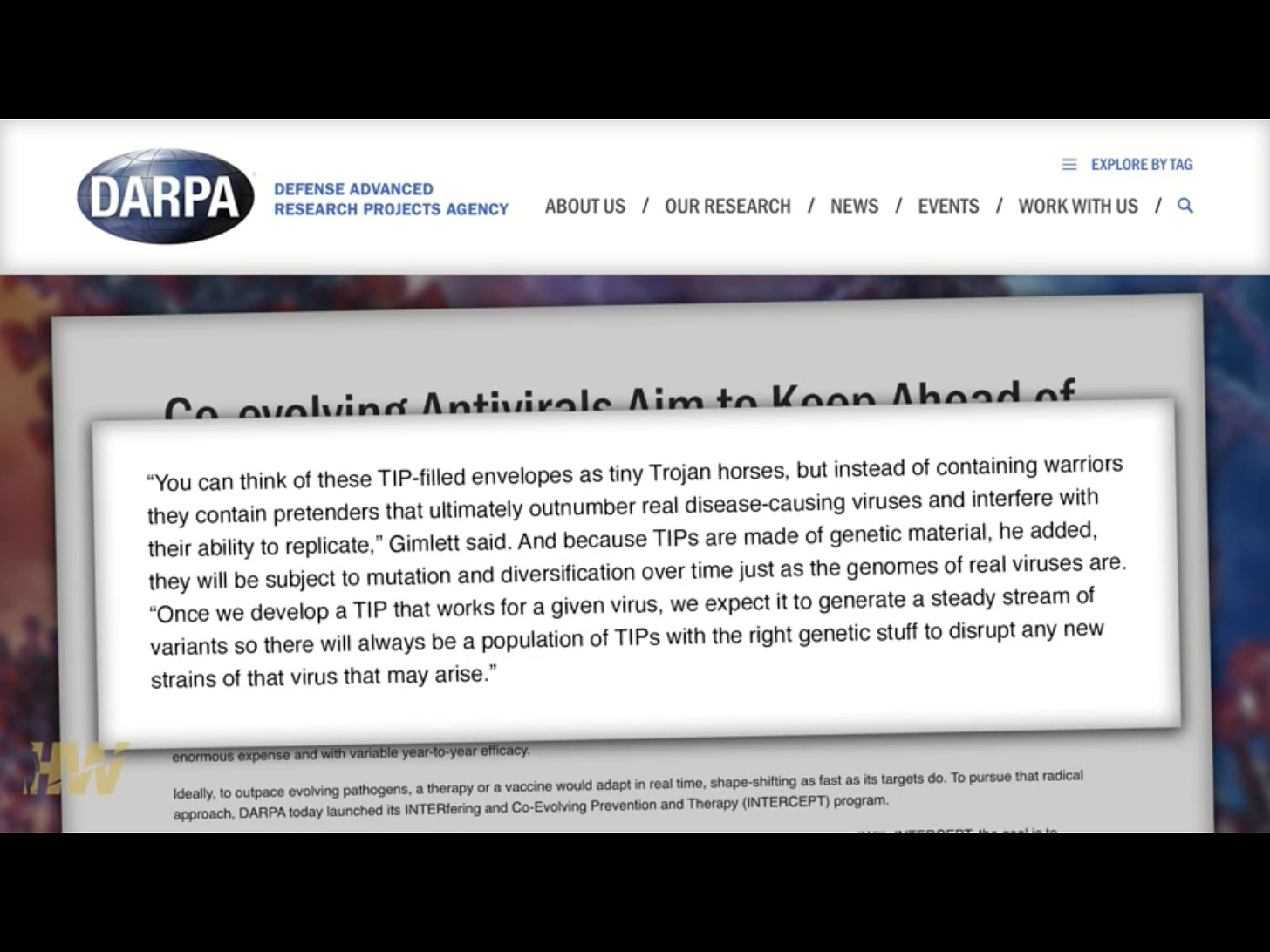
From DARPA
https://www.darpa.mil/news-events/2016-04-07a
DARPA Seeks First-in-Human Therapeutic Interfering Particles Targeting Respiratory Viruses
This shows the official government interest
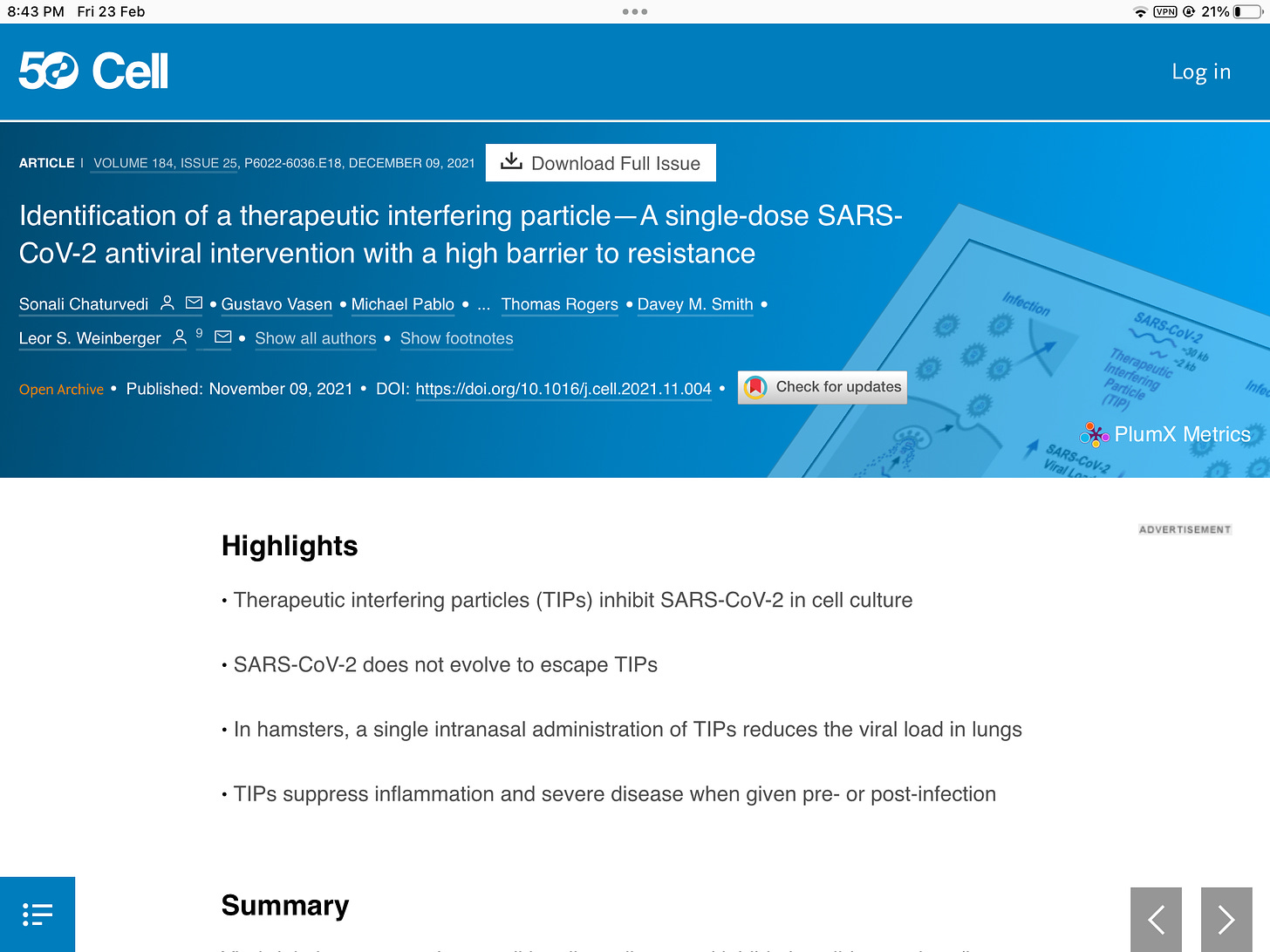
https://pubmed.ncbi.nlm.nih.gov/34838159/
This is the face behind all this, Leor Weinberger
In 2016
Engineering Our Way to Next Generation Therapies
Watch HERE
It has reached the level of government
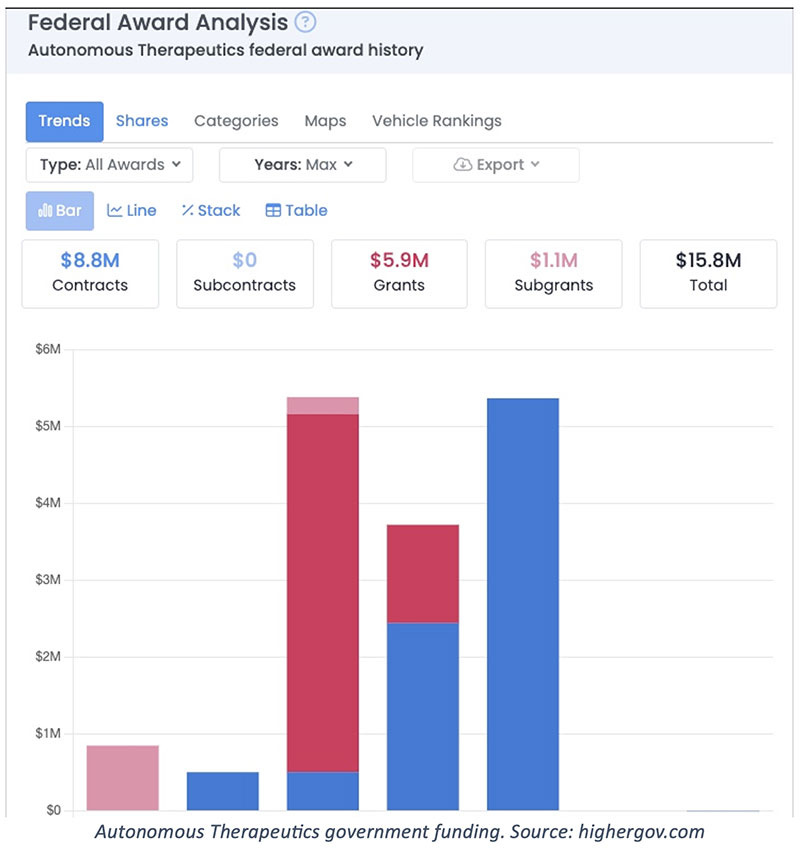
HHS issued a $4.8 million grant to VxBiosciences for “Autonomously Deploying,
Co-evolving SARS-CoV-2 Antiviral.” The grant was for engineering “therapeutic molecular parasites of SARS-CoV-2 that can co-adapt and transmit among infected hosts … acting as single-administration therapies that circumvent compliance issues.”
It has been incorporated into US government legislation
It seems the government and the military are so enthused about this new vaccine deployment technology that Congress tucked a law, the PREVENT Pandemics Act, into the 2023 omnibus appropriations bill to facilitate it. Among other things, the Act has a section dedicated to Platform Technologies that supports the “development and review of new treatments and countermeasures that use cutting-edge, adaptable platform technologies that can be incorporated or used in more
than one drug or biological product.”
Prevent Pandemics Act 2022
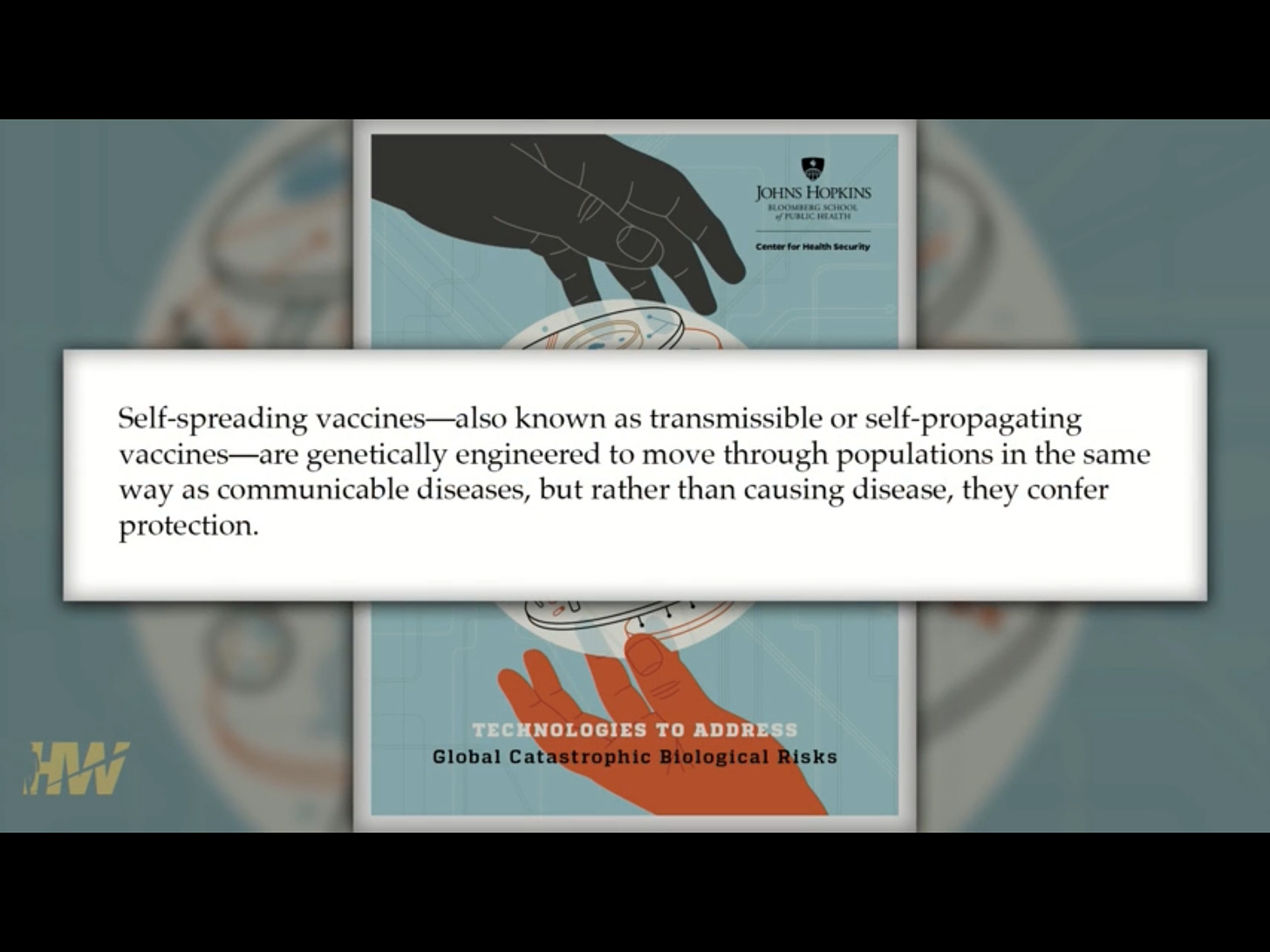
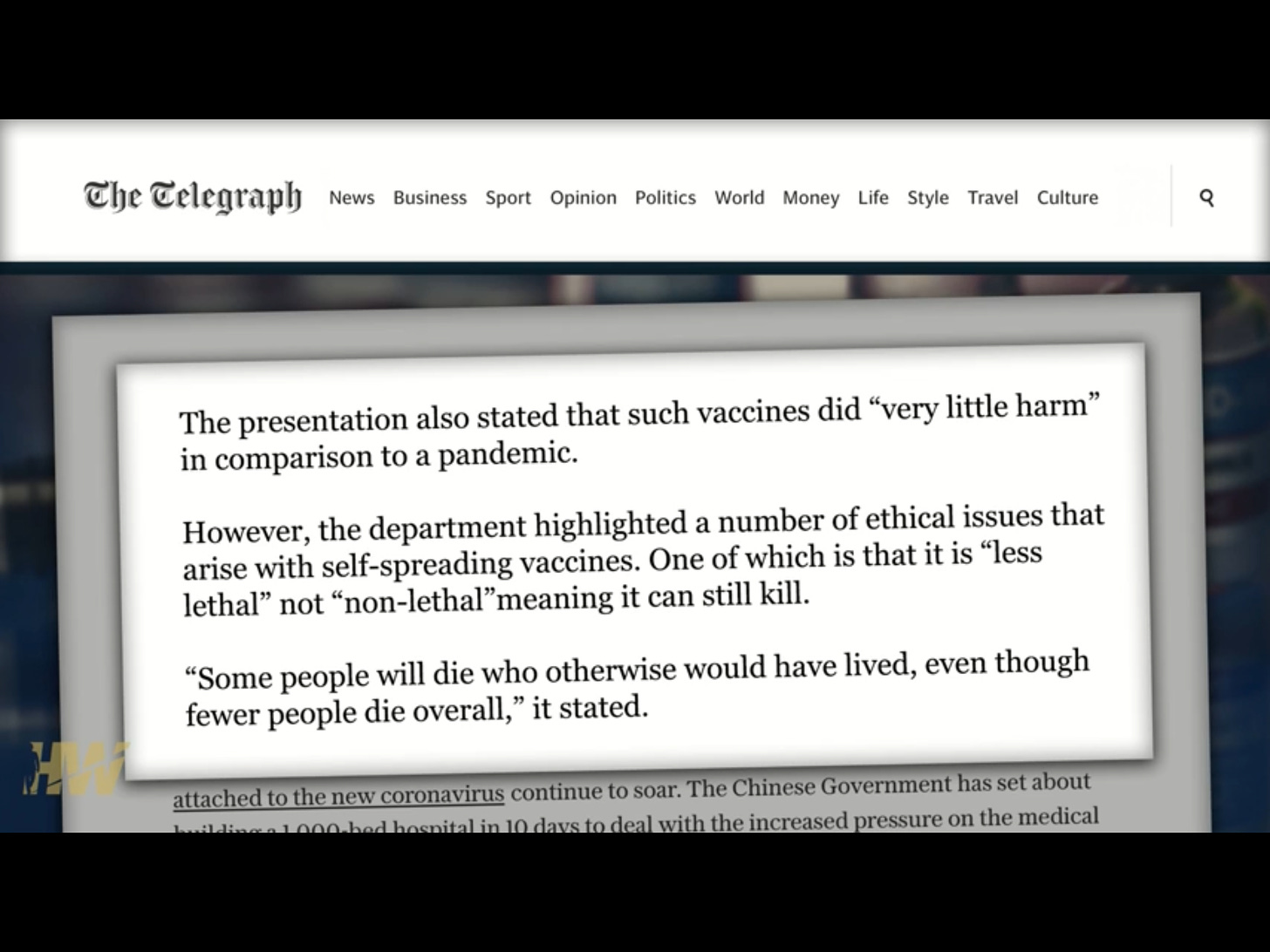
What can go wrong?
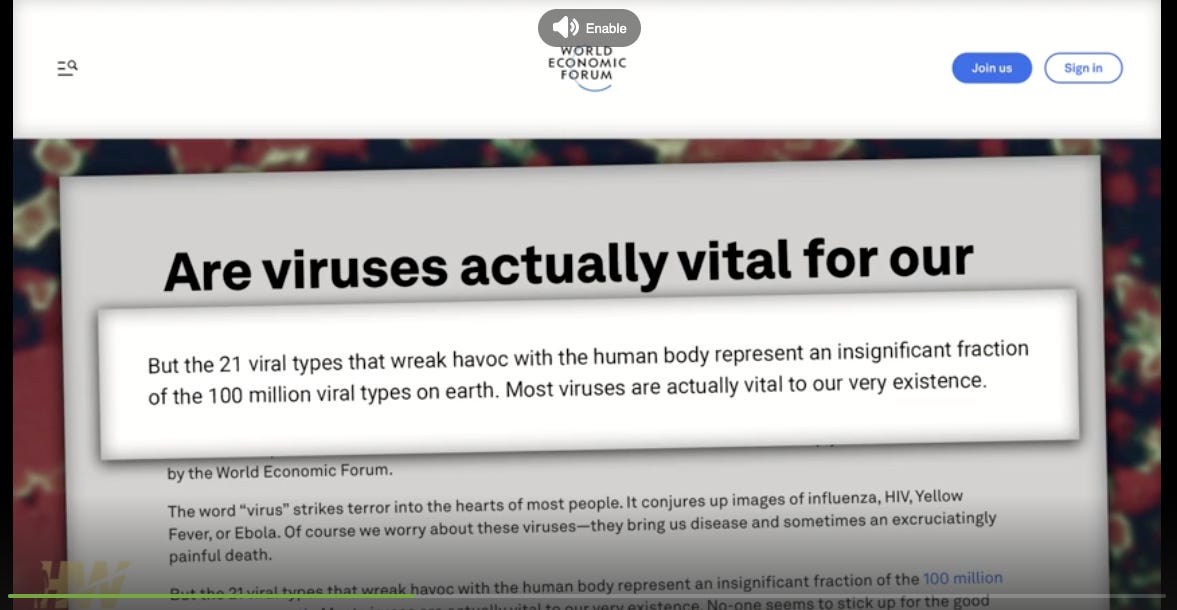
This is from no less than the World Economic Forum, albeit from back i
n 2015.
Read the article HERE